Downloads
Keywords:
Behavioral Authentication with Real-Time Anomaly Detection in Enterprise Logins
Authors
Abstract
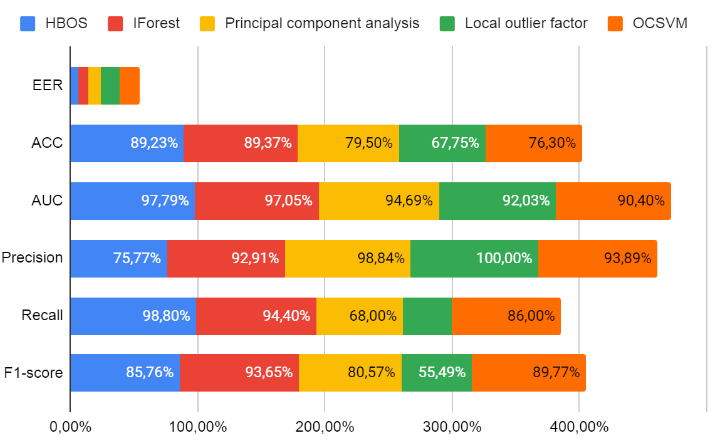
In this article, an approach to behavioral authentication with real‑time anomaly detection during corporate system logins is examined. The objective of this study is to design and evaluate an architecture for continuous biometric user verification based on interaction dynamics, including cursor speed and trajectory curvature, inter-keystroke time intervals, and device micro-movements, while ensuring processing latency of below 100 ms under loads of up to tens of thousands of logins per second. It justifies because of the high percentage of incidents that happen out of credential compromise and low coverage of MFA, hence a continuous effort removal of friction for legitimate users. The novelty in this solution is introduced by the streaming architecture provided by Kafka and Flink-based applications, combined with telemetry normalization techniques using z-scores and robust scaling methods, together with an ensemble hybrid model consisting of a one-class autoencoder, relative attention, Isolation Forest, and a semi-supervised SSDLog scheme. Added value is brought by a dynamic threshold calibration mechanism that takes into account daily and weekly seasonality as well as federated learning and differential privacy noise mechanisms that satisfy privacy requirements. Findings present here will show that this proposed system ensures a median analysis latency of 26 ms, where the 99th percentile does not cross 51 ms, equal‑error rate around about 1% at verification frequency of 0.7 s, reduces the number of interactive MFA challenges almost threefold for non‑critical accounts and ensures adaptation to user behavior drift through continuous self‑learning and feedback from SOC analysts. This article will be helpful to information security specialists, authentication system developers, and IT architects of large corporate infrastructures.
Article Details
Published
Issue
Section
License

This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.

